Palo Alto Networks
PAN TRAPS Endpoint Protection (Coxtex XDR)

Palo Alto Networks Traps replaces traditional antivirus with multi-method prevention, a proprietary combination of purpose-built malware and exploit prevention methods that protect users and endpoints from known and unknown threats. Traps prevents security breaches, in contrast to breach detection and incident response after critical assets have already been compromised.
Traps uses an entirely new and unique approach to prevent exploits. Instead of focusing on the millions of individual attacks, or their underlying software vulnerabilities, Traps focuses on the core exploitation techniques used by all exploit-based attacks. Each exploit must use a series of these exploitation techniques to successfully subvert an application.
Traps renders these techniques ineffective by blocking them the moment they are attempted. Organizations using Traps can run any application, including those developed in-house and those that no longer receive security.
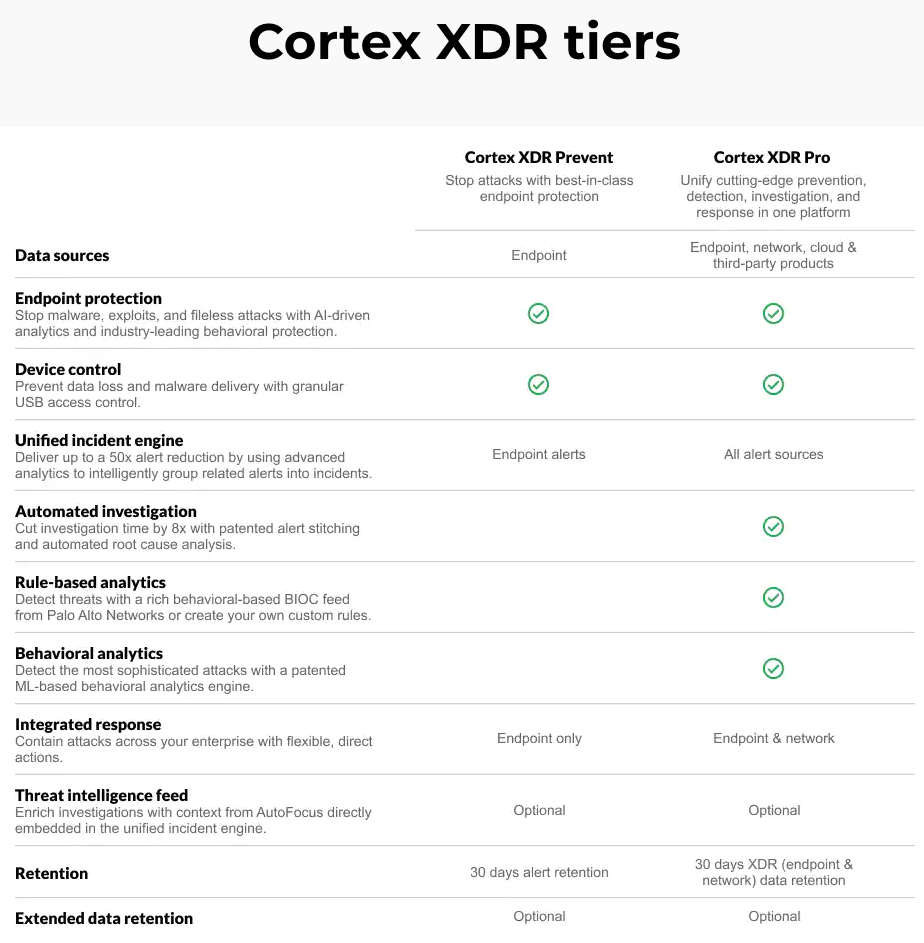
TRAPS is now part of Cortex XDR Prevent, providing the endpoint protection component.
Traps uses an entirely new and unique approach to prevent exploits. Instead of focusing on the millions of individual attacks, or their underlying software vulnerabilities, Traps focuses on the core exploitation techniques used by all exploit-based attacks. Each exploit must use a series of these exploitation techniques to successfully subvert an application.
Traps renders these techniques ineffective by blocking them the moment they are attempted. Organizations using Traps can run any application, including those developed in-house and those that no longer receive security.
TRAPS is now part of Cortex XDR Prevent, providing the endpoint protection component.
Multi-Method Malware Prevention
Static Analysis via Machine Learning
This method delivers an instantaneous verdict for any unknown executable file before it is allowed to run. Traps examines hundreds of the file’s characteristics in a fraction of a second, without reliance on signatures, scanning or behavioral analysis.
Cloud Based Malware Analysis
This method leverages the power of Palo Alto Networks WildFire™ cloud-based malware analysis environment to rapidly detect unknown malware and automatically reprogram Traps to prevent known malware.
WildFire eliminates the threat of the unknown by transforming it into known in about 300 seconds.
WildFire eliminates the threat of the unknown by transforming it into known in about 300 seconds.
Trusted Publisher Restrictions
This method allows organizations to identify executable files that are among the “unknown good” because they are published and digitally signed by trusted publishers—entities that Palo Alto Networks recognizes as reputable software publishers.
Policy Based Restrictions
Organizations can easily define policies to restrict specific execution scenarios, thereby reducing the attack surface of any environment. For example, Traps can prevent the execution of files from the Outlook® “temp” directory or prevent the execution of a particular file type directly from a USB drive.
Policy Based Overrides
This method allows organizations to define policies, based on the hash of an executable file, to control what is allowed to run in any environment and what is not. This fine-grained whitelisting (or blacklisting) capability controls the execution of any file, based on user-defined conditions that tie into any object that can be defined with Microsoft® Active Directory®.
About Us | Contact Us | Privacy Policy | EOL
© 2023 Altaware, Inc. | All rights reserved.
949-468-0020
CYBER SECURITY skills in ORANGE COUNTY, CA
Remote cyber security skills/services within the USA