ForeScout Technologies

ForeScout Technologies is a leading provider of automated security control solutions for Fortune 1000 enterprises and government organizations. With ForeScout, organizations can accelerate productivity and connectivity by enabling people to access corporate network resources where, how and when needed without compromising security.
ForeScout’s CounterACT platform for network access control, mobile security, threat prevention and endpoint compliance empower access agility while preempting risks and eliminating remediation costs.
ForeScout’s CounterACT platform for network access control, mobile security, threat prevention and endpoint compliance empower access agility while preempting risks and eliminating remediation costs.

Overview
ForeScout CounterACT is an automated security control platform that delivers real-time visibility and control of all devices on your network. ForeScout CounterACT automatically identifies who and what is on your network, controls access to your network resources, measures compliance with your security policies, blocks network threats, and remediates endpoint security violations when they occur. CounterACT makes you smarter, your network more secure, and your staff less busy by automating tasks that are currently laborious.
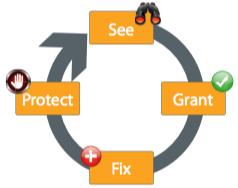
ForeScout CounterACT employs a proven approach for IT risk management, as shown in the diagram. Every device that accesses your network is identified, controlled, remediated (if you wish), and continuously monitored to ensure compliance and protection.
ForeScout CounterACT employs a proven approach for IT risk management, as shown in the diagram. Every device that accesses your network is identified, controlled, remediated (if you wish), and continuously monitored to ensure compliance and protection.
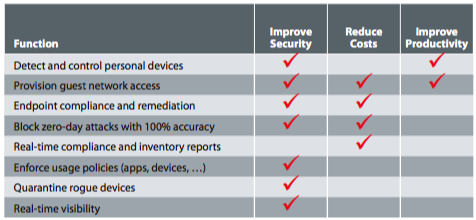

Appliances
ForeScout Appliances
ForeScout CounterACT is a real-time network security platform that delivers dynamic visibility and control of all devices on your network. ForeScout CounterACT automatically identifies who and what is on your network, controls access to your network, measures compliance with your security policies, blocks network threats, and remediates endpoint security violations when they occur. CounterACT makes you smarter, your network more secure, and your staff less busy by automating tasks that are currently laborious.
ForeScout CounterACT employs a proven approach for IT risk management, as shown in the diagram below. Every device that accesses your network is identified, controlled, remediated (if you wish), and continuously monitored to ensure compliance and protection.
ForeScout CounterACT employs a proven approach for IT risk management, as shown in the diagram below. Every device that accesses your network is identified, controlled, remediated (if you wish), and continuously monitored to ensure compliance and protection.
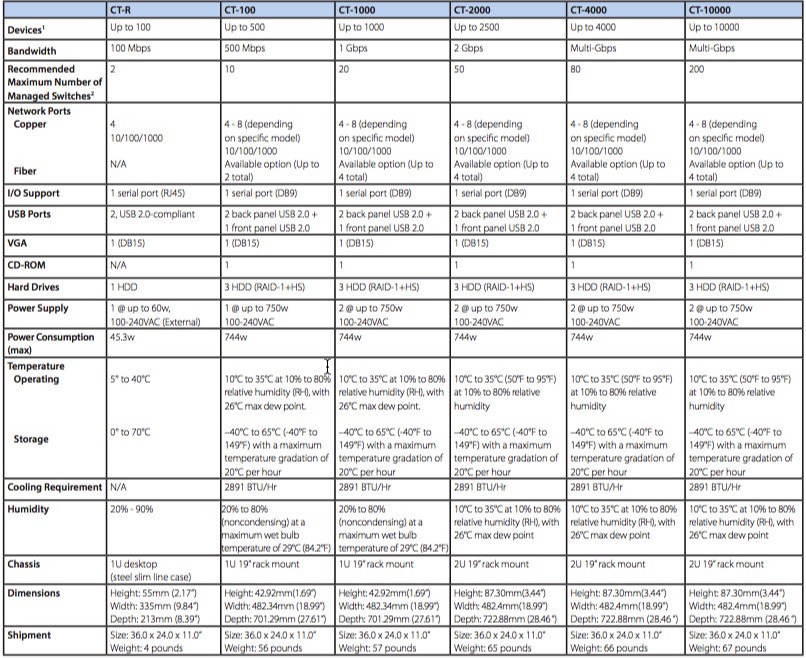
Show Hardware Appliance Matrix

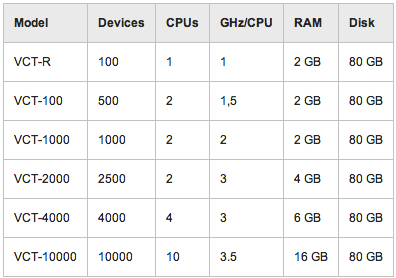
Show Virtual Appliance Matrix

-
CT-R (100 Devices)Devices: 100
Bandwidth: 100 Mbps
Copper RJ-45 network ports: 4
Fiber network ports: N/A -
CT-100 (500 Devices)Devices: 500
Bandwidth: 500 Mbps
Copper RJ-45 network ports: 4-8 (10/100/1000) depending on model
Fiber network ports: Optional up to 2 total -
CT-1000 (1,000 devices)Devices: 1,000
Bandwidth: 1 Gbps
Copper RJ-45 network ports: 4-8 (10/100/1000) depending on model
Fiber network ports: Optional up to 4 total -
CT-2000 (2,500 devices)Devices: 2,500
Bandwidth: 1 Gbps
Copper RJ-45 network ports: 4-8 (10/100/1000) depending on model
Fiber network ports: Optional up to 4 total -
CT-4000 (4,000 devices)Devices: 4,000
Bandwidth: Multi-Gbps
Copper RJ-45 network ports: 4-8 (10/100/1000) depending on model
Fiber network ports: Optional up to 4 total -
CT-10000 (10,000 devices)Devices: 10,000
Bandwidth: Multi-Gbps
Copper RJ-45 network ports: 4-8 (10/100/1000) depending on model
Fiber network ports: Optional up to 4 total -
Beyond 10,000 devicesIf your organization is very large or geographically dispersed, you might require multiple appliances. You can manage multiple CounterACT appliances from a single management console known as ForeScout CounterACT Enterprise Manager. This is also sold as an appliance and licensed by the number of appliances that the Enterprise Manager covers.
-
Virtual ApplianceSupported operating systems:
- VMware ESX and ESXi v3.5 update 5
- VMware ESX and ESXi v4.0 update 2
- VMware ESX and ESXi v4.1 update 1
- VMware ESX and ESXi v5.1 update 1
- Or, Microsoft Hyper-V 2008 R2 with LIC v3.2 and above.

Open all Close all
MDM Integration
Mobile Device Management (MDM) systems are gaining rapid adoption among enterprises that wish to better manage the plethora of smartphones and tablet computers that are in common use by businesspeople. MDM systems can help IT security managers secure the sensitive corporate data that is frequently stored on such devices.
In conjunction with your MDM system, ForeScout CounterACT with the MDM Integration Module provides unified security policy management for everything on your network regardless of the type of device (PC, Mac, Linux, tablet, smartphone), the type of connection (wired, wireless, VPN) or the ownership of the device (corporate or personal). Benefits include:
- MDM systems can only see and manage devices that have already been enrolled in the MDM system.
- MDM systems typically do not control access to the network, they typically control access to applications (for example, Microsoft Exchange). Thus, MDM does not prevent unauthorized access to data on the network, nor does MDM prevent infected or compromised devices from attacking the network.
- MDM systems are often operated as another IT management silo, with another set of management screens, separate policies, and separate reports. Even worse, the MDM system is often managed by a different group of people than are responsible for computer security.
Improved Visibility
Enhanced Security
Policy Enforcement
Operational Efficiency
Easier Management and Reporting
Compare the ForeScout CounterACT offering with various MDM options.
-
Operational Management
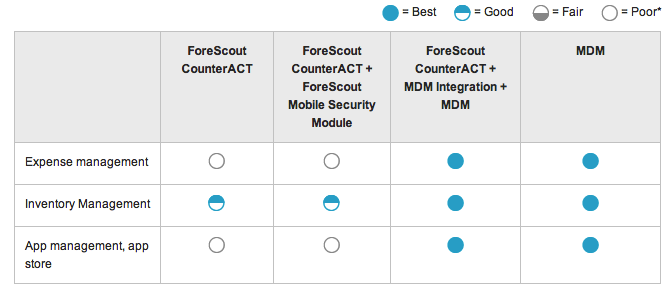

-
Network Security
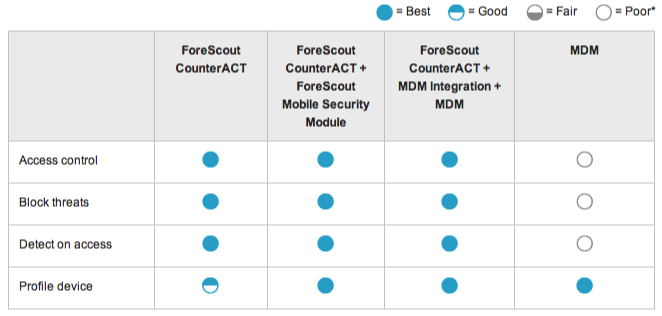

-
Device and Data Security
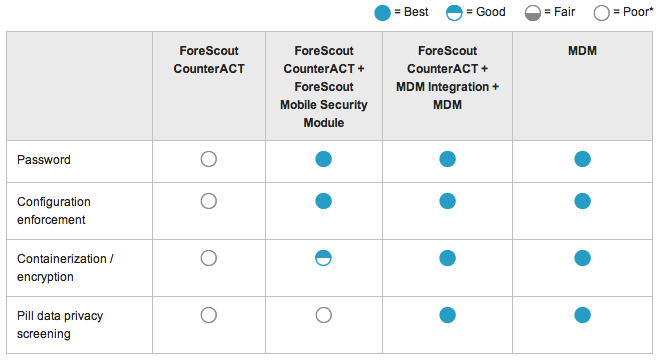

-
Unified visibility and network access policy
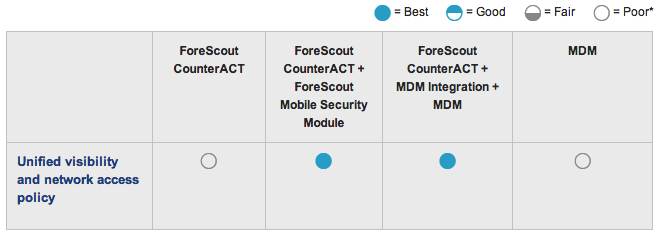

-
User Impact
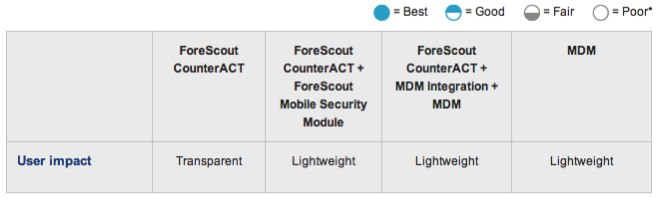

-
Price
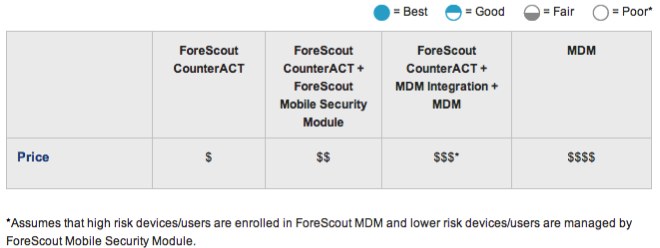

Open all Close all
Actions
ForeScout NAC Active Control Actions
Alert & Remediate
Open trouble ticket
Send email notification
SNMP traps
Start application
Run script to install application
Auditable end-user acknowledgement
HTTP browser hijack
Trigger other endpoint solution to remediate endpoint
Limit Access
Deploy a virtual firewall around the device
Reassign the device to a VLAN with restricted access
Update ACLs on switches, firewalls and routers to restrict access
Captive portal (via DNS hijack)
Automatically move device to a guest network
Move & Disable
Move device to quarantine VLAN
Block access with 802.1x
Alter login credentials to block access, VPN block
Block access with device authentication
Turn off switch port (802.1x, SNMP)
Wi-Fi port block
Terminate applications
Disable peripheral device
About Us | Contact Us | Privacy Policy | EOL
© 2023 Altaware, Inc. | All rights reserved.
949-468-0020
CYBER SECURITY skills in ORANGE COUNTY, CA
Remote cyber security skills/services within the USA