Header
Lorem ipsum dolor sit amet,consectetur adipiscin elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco commodo consequat. Duis aute irure dolor in reprehenderit in fugiat nulla pariatur. Excepteur sint occaecat non proident, sunt officia deserunt mollit anim id est laborum.
PAN Firewalls
Select PAN firewall below based upon throughput
-
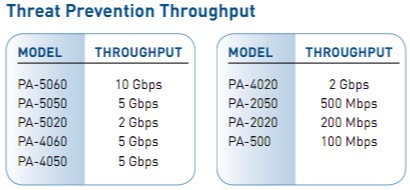
Branch/Small OfficePA-220 - Consider PA-4xx Series for new purchases
 The PA-220 provides you interactive visibility and control of applications, users, and content at throughput speeds of up to 500 Mbps. You get redundant power input for increased reliability, a fanless design for quiet operation, and solid state disks to remove any moving parts. The PA-220 also simplifies the deployments of large numbers of firewalls through the USB port.
The PA-220 provides you interactive visibility and control of applications, users, and content at throughput speeds of up to 500 Mbps. You get redundant power input for increased reliability, a fanless design for quiet operation, and solid state disks to remove any moving parts. The PA-220 also simplifies the deployments of large numbers of firewalls through the USB port.
For new purchases, consider the PA-440 to PA-460 instead.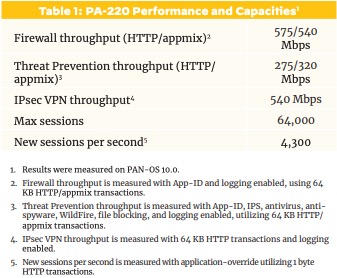
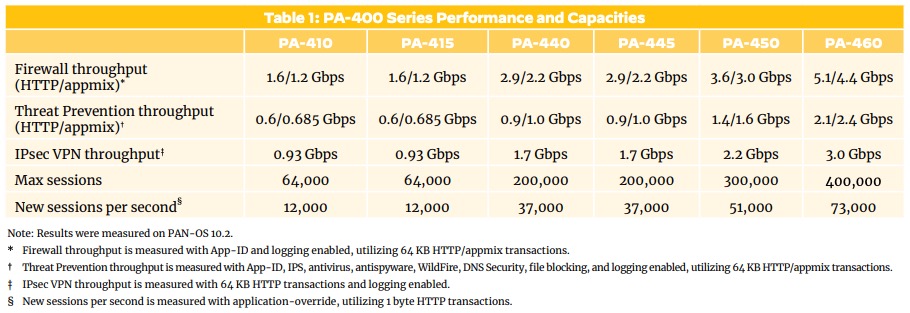
 PA-4xx - NEW MODELS
PA-4xx - NEW MODELSNOTE: The PA-410/PA-415 does not have on box logging

 PA-8xx Series (** consider PA-4xx or PA14xx **)NOTE: There are two dedicated HA ports for clustering
PA-8xx Series (** consider PA-4xx or PA14xx **)NOTE: There are two dedicated HA ports for clustering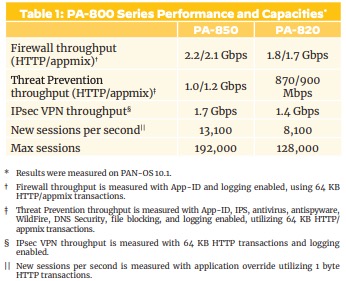

-
Small-Medium OfficePA-14xx Series - New Series

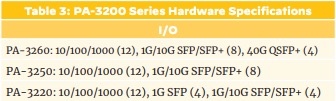
 PA-32xx Series
PA-32xx Series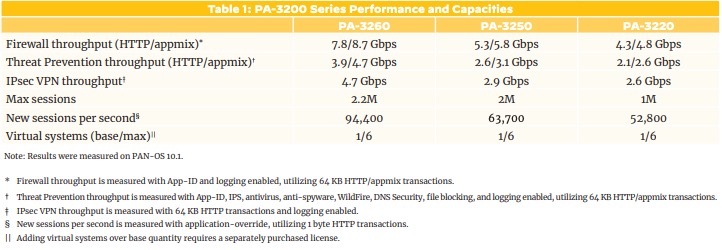
-
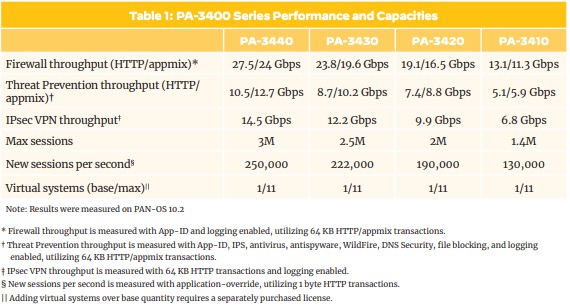
Over 10 GbpsPA-34xx Series - NEW MODEL
 PA-5450 - NEW MODEL
PA-5450 - NEW MODEL
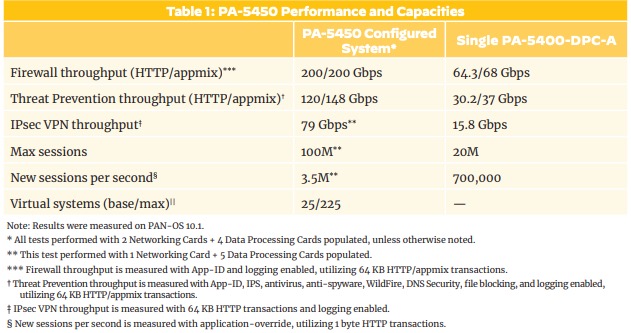 PA-52xx Series
PA-52xx Series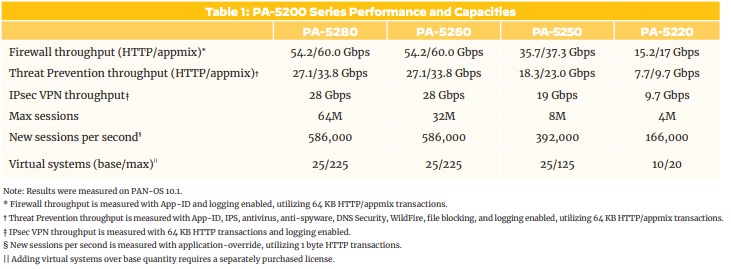
 PA-7000 SeriesPower, intelligence, simplicity and versatility for enterprise and service provider deployments.
PA-7000 SeriesPower, intelligence, simplicity and versatility for enterprise and service provider deployments. -
VirtualVM-Series virtual firewalls help your organization safely transform its virtualized infrastructure into business innovation and competitiveness.
NOTE: Firewall performance can vary with PAN-OS firmware releases. Upgrade to current releases for improved results and protection. Specifications for comparison purposes only. Refer to the respective product specsheets for the more up-to-date information.
Got any questions about selecting the best PAN firewall for your needs, please contact us!
PAN Subscriptions
-
Threat Prevention (IDP/AV/malware)
Palo Alto Networks IDP Capabilities
Drive-by downloads are increasingly popular yet very difficult to protect against. Unsuspecting users can inadvertently download malware without knowing, merely by visiting their favorite web page and clicking on an image. Palo Alto Networks next generation firewalls can identify drive-by downloads and present users with a warning to ensure that the download action is desired.Unlike many current solutions that may use a single CPU or an ASIC/CPU combination to try and deliver enterprise performance, Palo Alto Networks utilizes a purpose-built platform that uses dedicated processing for threat prevention along with function-specific processing and dedicated memory for networking, security and management. Using four dedicated types of processing means that key functions are not competing for processing cycles with other security functions, as is the case in a single CPU hardware architecture. The end result is low latency, high performance throughput with all security services enabled.The Palo Alto Networks threat research team is a world-class research organization dedicated to the discovery and analysis of threats, applications and their respective network behavior. Through internal research, third party relationships with software vendors (e.g., Microsoft) and the same research organizations used by other leading security vendors, customers are assured that Palo Alto Networks is providing them with the best network threat protection and application coverage. -
URL FilteringPalo Alto Networks includes and optional feature license to enable URL filtering. Unlike other competitive offerings that are user based, this is licensed on a per chassis basis which offers amazing price savings and fully protects all users. URL filtering is based upon both a locally cached large database for performance and hosted / cloud based support for even more URLs.
Select Palo Alto Networks URL filtering from us as a viable and cost effect alternative to Websense Enterprise or Websense Express. URL filtering is licensed by the chassis (unlimited users) and not per seat making it a more affordable alternative. URL filtering works in conjunction with User-ID for user based and/or group policy setting.
Stand-alone URL filtering solutions are insufficient control mechanisms because they are easily bypassed with external proxies (PHproxy, CGIproxy), evasive tools (TOR, UltraSurf, Hamachi) and remote desktop access tools (Yoics!, RDP, SSH).PAN URL test site works with Palo Alto Networks URL filtering directly from Palo Alto Networks.Blocked sites (web site blacklisting)Allowed sites (web site whitelisting)Blocking proxy sites, malware sites and other risky sitesBlocked based on categories (e.g. porn, nudity, weapons, gambling and over 70+ categories)Allow just appropriate web sitesCoached and password override optionsUser and/or group membership based policiesFacilitate SSL decryptions policesCustomizable URL database categoriesOn box reporting, no separate database or reporting servers!URL Activity Reporting and Logging
A set of pre-defined or fully customized URL filtering reports provides IT departments with visibility into URL filtering and related web activity including:
User activity reports
An individual user activity report shows applications used, URL categories visited, web sites visited, and a detailed report of all URLs visited over a specified period of time.
URL activity reports
A variety of top 50 reports that display URL categories visited, URL users, web sites visited, blocked categories, blocked users, blocked sites and more.
Real-time logging
Logs can be filtered through an easy-to- use query tool that uses log fields and regular expressions to analyze traffic, threat or configuration incidents. Log filters can be saved and exported and for more in-depth analysis and archival, logs can also be sent to a syslog server.FAQs - PAN URL
Lets start with the basics, both do URL filtering. Both support using categories to allow or disallow access (e.g. nudity, gambling, etc.) Palo Alto Networks (PAN) is complemented with a cloud service for dealing with less common URLs beyond the millions maintained on the chassis.
- You pay a single recurring license for the chassis, no per user fees (translation: you save money now and later)
- You don't need a separate reporting system for the database
- No OS backups, database backups to worry about
- No Windows or other OS patches to deal with
- Web 2.0 is more about applications than URLs, you get a single pass high-speed solution that adds next generation application awareness
- HA for High Availability, sure, of course
- You can support remote user policy control with PAN Global Protect
- PAN includes decryption to further deal with evasion
- PAN includes data filtering capabilities
- User tracking, of course
- Log support on device and off with syslog
- Deployment options include span/mirror port, inline virtual wire, layer 2 and layer 3. You can even mix and match and with lots of ports.Yes, covered.Allow - Allow without logging
Alert - Allow and log
Continue (coached access) - Notify the user that perhaps this site might be inappropriate and allow them to continue and log that
Override - Password override option.
Policies can be defined by user, group membership, IP address, schedules (time of day), applications, ports. It allows site whitelisting and blacklisting.
You can even define QoS (Quality of Service) restrictions.Both are excellent solutions, both are still actively sold and supported. Palo Alto Networks has made their own URL filtering available to provide another option at the same cost. By owning their own list, it provides PAN with the capability to quickly mark or note URLs with malware as opposed to waiting for updates from another provider. This solution works great with the WildFire solution as new malware may be detected via WildFire customers and then all customers with PAN based URL filtering will benefit from URL categorization changes.
Both solutions use categories for allow, alerting, blocking, etc. The categories are not identical, but similar. There is a tool for converting from Brightcloud URL filtering to Palo Alto Networks db URL filtering, but not in the reverse direction. In the case of Palo Alto Networks URL filtering, subdomains can be categorized differently than the main domain. This provides better categorization of larger sites that have a wide variety of content.Palo Alto Networks is all about performance using a single pass design to only inspect the traffic once for firewall policy, threats / malware, application identification, data content matching and URL filtering. This avoids additional latency imposed by other solutions including competitive UTM offerings. -
WildFire
PAN WildFire Subscription
WildFire exposes previously unseen malicious executable files by directly observing their behavior in a secure virtualized environment. This direct analysis quickly and accurately identifies new malware, leading to the automated creation of new signatures that are distributed to all Palo Alto Networks devices via the current threat prevention subscription service.
When the firewall encounters an unknown .EXE or .DLL that has been delivered by any application, even those that are encrypted with SSL, the file can be submitted to the WildFire virtualized sandbox, where Palo Alto Networks can directly observe more than 70 malicious behaviors that can reveal the presence of malware. Submissions can be made manually or automatically based on policy.
When a sample is identified as malware, the sample is passed on to WildFire's signature generator, which automatically generates a signature for the sample and tests it for accuracy. The new signature is then distributed in the next content update. Palo Alto Networks also develops signatures for the all-important command and control traffic, enabling staff to immediately disrupt the communications of any malware inside the network.
WildFire intelligence and forensics
In addition to providing protection, administrators have access to a wealth of actionable information about the detected malware through the WildFire portal. A detailed behavioral report of the malware is produced, along with information on the user that was targeted, the application that delivered the malware, and all URLs involved in the delivery or phone-home of the malware.
Integration of firewall and the cloud
WildFire makes use of a customer's on-premises firewalls in conjunction with Palo Alto Networks cloud-based analysis engine to ensure in-line performance, while using the cloud to deliver the fastest protections for all enterprise locations.FAQs - PAN WildFire
In our opinion, it can be. WildFire will continue to evolve, but already offers near realtime protection against new unknown malware by using a cloud based virtual sandbox. Palo Alto Networks will continue to develop and expand the product. The firewall is the proper location to perform this inspection. PAN firewalls offer tremendous real performance and now leverage the cloud to add further protections.
FireEye is a great point solution, now with Palo Alto Networks this becomes another feature on an already existing powerful security gateway. Did we mention this saves a lot of money compared to multiple point solutions?All customers with Threat Prevention license can benefit from WildFire updates, but typically this is a 48 hour delay. This is a tremendous value add that Palo Alto Networks has added to further secure networks. Optionally use GlobalProtect to secure roaming mobile platforms.
However, if even more protection you can subscribe to a WildFire subscription to get threat updates in less then an hour, on average every 30 minutes. This offers superior zero day (0 day) protection versus waiting 24 hours for a threat subscription update.Endpoint software is based upon signature matches. In today's threat landscape with polymorphic (rapidly changing) malware, signatures provide limit protection. Based upon on some studies, as much as 70% of malware could be undetected with purely signature based desktop or laptop agent based software protection.Potential threats are sent to the cloud near realtime (you determine the frequency). The virtual sandbox analyzes the characteristics of the attachment to determine if it could be malicious based upon those actions. If it is, the PAN WildFire service will create a new threat signature match and release that as an update to the PAN threats database. You can set your PAN to check hourly for new signatures and apply those on the firewall automatically. This also means that as a valid subscriber to the threats database that you get additional protection from all the other deployed devices across the world.
With an optional WildFire subscription, updates on average can be received every 30 minutes, no more than a one hour delay. Again, this requires the optional WildFire subscription to get updates within the hour versus after 24 hours.As part of WildFire and having a support account, you get access to your own WildFire portal and can view what was found for your own PAN firewalls. It will let you know what has been determined to not be a threat, is still pending an analyses or was in fact a new threat. Please note, as of PANOS 5.s, there have been additional enhancements to WildFire and on box integration versus could portal login.It inspects EXE and DLL files. If they are unknown, based upon signatures, then they are submitted to a virtual sandbox in the cloud where it is checked to see if it exhibits any of roughly 70 malicious behaviors that malware might be exhibiting. It then tracks and reports those observations via a hosted portal site that the end customer can access. It then notes the signature and distributes that to all PAN firewalls with current threat licenses preventing further spread of the malware.
With the optional Palo Alto Networks WildFire subscription, signatures updates are applied much more frequently, this is especially important during the critical first 24 hours. -
GlobalProtect
PAN- Global Protect
Consistent Policy & Enforcement for All Users
GlobalProtect extends the same next-generation firewall-based policies that are enforced within the physical perimeter to all users, no matter where they are located. In effect, GlobalProtect establishes a logical perimeter that extends policy beyond the physical perimeter. Employees working from home, on the road for business, or logging in from a coffee shop will be protected by the logical perimeter in the same manner that they would be if they were working from their office.FAQs - Global Protect
It is a software agent that that extends the protection of a corporate perimeter to remote user devices thereby applying all the same policies and protections to remote users. This includes URL filtering, threat inspection, visibility, etc. already being provided to local users. It does this by utilizing three components:
1) Existing corporate PAN firewall(s) acting as gateways.
2) A GlobalProtect portal for management including host configuration characteristics. The portal deals with authentication and downloading of new agent software if needed for the client.
3) An agent that communicates to the portal, creates an encrypted session to the gateway(s) and it creates a Host Information Profile (HIP) of the client device.
4) Desktops, laptops and mobile platforms are support (depending upon the license).Consistent policy and central management to apply to local or remote users thereby simplifying policy enforcement without additional hardware or additional management systems. Lets not forget not having to buy another appliance just for remote users.The portal management runs on the Palo Alto Networks firewall (High Availability option too). The user software agents are supported on: Microsoft Windows XP, Microsoft Windows 7, Microsoft Windows Vista and Apple IOS.PAN firewalls are used as the enforcement appliances. From a license perspective, a portal license must be purchased for the unit (or more for redundancy) doing the portal management. Licenses for GlobalProtect are required on all desired PAN units acting as gateways (this does not have to be all the deployed PANs, just those desired as remote access gateways). Support is purchased for updates to the software along with technical support.
GP (Global Protect) is included in a lite (free) basic form which supports a single gateway and portal (without the host endpoint enforcement). If you want any of the following capabilities, you need to purchase the optional GP gateway subscription:- Endpoint enforcement via PAN HIP profiles
- Mobile support (Apple iOS or Android) versus just MS Windows or MacOS
- To use the new GP clientless VPN capability
- To enable multiple gateways (read release notes for more clarification)
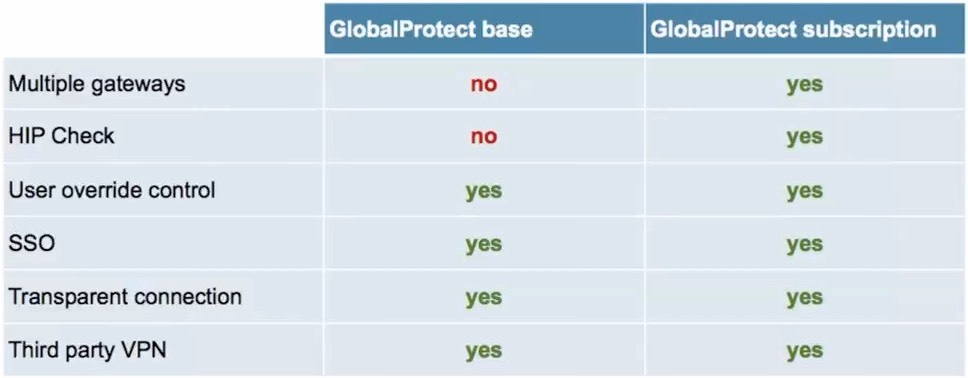
 NOTE: Starting with PANOS 7.0, you no longer need to purchase the GP Portal License.!Yes, split tunneling policies can be defined via the portal management system.
NOTE: Starting with PANOS 7.0, you no longer need to purchase the GP Portal License.!Yes, split tunneling policies can be defined via the portal management system.
NOTE: The behavior does change starting with PANOS 7.0, please read the release notes to better understand the changes.Basic SSL VPN connectivity via a lite version of GP is already included on the PAN base systems to address remote access for users of Windows and MacOS. GlobalProtect license option extends the features (see buy/not buy question).
GlobalProtect acts as a transparent SSL VPN regardless of how users connect to the Internet and making sure those connections remain encrypted. GP will use IPSec by default for performance benefits, but can fallback to SSL where networks disallow IPSec traffic.- Operating system and patch level
- Host anti-malware version
- Host firewall version
- Disk encryption
- Data backup products
- Customized host conditions
NOTE: Above are enabled via HIP profiles on the portal and require optional Global Protect license(s).You can control where users are placed in terms of a security zone. Users can be placed in the same internal network (typically Trust) zone or they can have their tunnels terminated in a different secure zone (e.g. RemoteUsers) and then use security policies tied to usernames and/or applications to control and restrict access. This includes threat inspection features, spyware, malware, ant-virus, etc. Sounds like a great idea, right?It can be done, but you need to talk with your PAN administrator and have them check the Palo Alto Networks support site. We're not going to help IT users remove a corporate control from their desktops except via the official corporate administrators. Yes, GP is an excellent tool for enforcing corporate policies and as such should not be easy to disable or remove by unauthorized users.
If you would like us to work with the IT department, we are available for Professional Services via a billable engagement. -
DNS Security ServicesUse predictive analytics to disrupt attacks that use DNS for command and control (C2) or data theft. Tight integration with Palo Alto Networks Next-Generation Firewalls gives you automated protection and eliminates the need for independent tools.
-
SD-WANSecure and reliable software-defined WAN that delivers an optimal user experience for cloud applications from your branches and retail locations, without compromising security.
-
Enterprise Data Loss PreventionAs a cloud service, Palo Alto Networks Enterprise DLP solution discovers, monitors and protects an organization’s sensitive data, such as PII and intellectual property, minimizing the risk of data breaches and enhancing data privacy and compliance. Embedded in Prisma SaaS and Prisma Access, our service uses the same configuration and detection rules at both control points, providing consistent data protection everywhere, eliminating the need of creating and maintaining separate sets of policies.
PAN TRAPS
Find out more on our TRAPS specific page.
PAN Support
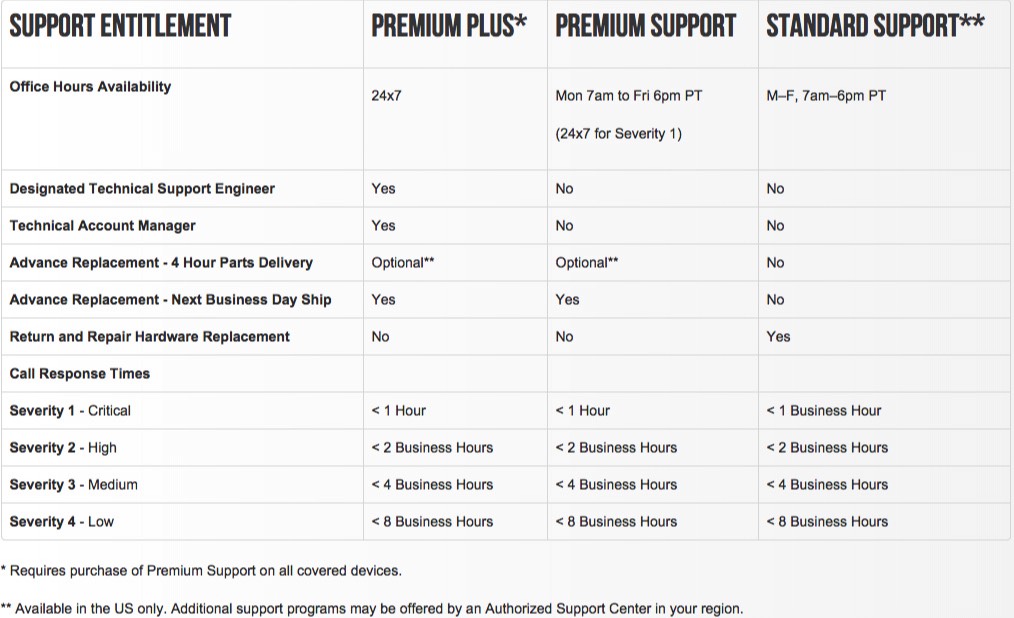

Severity 1 – Critical: Every 4 hours until resolved or a workaround is in place.
Severity 2 – High: Every business day until resolved or a workaround is in place.
Severity 3 – Medium: Every 3 business days until resolved.
Severity 4 - Low: Once per business week until resolved.
Severity Definitions
Severity 1 – Critical: Product is down and critically affects customer production environment. No workaround yet available.
Severity 2 – High: Product is impaired and customer production is up but impacted. No workaround yet available.
Severity 3 – Medium: A product function has failed and customer production is not affected. Support is aware of the issue and there is a workaround available.
Severity 4 – Low: Product function is not impaired and no impact to customer business. Includes feature, information, documentation, how-to and Enhancement requests from the customer.